New phishing vector possible in Microsoft Teams
Microsoft announced on the 26th of January that they will enable a new collaboration feature with external customers and partners. This new feature makes it possible to chat with any teams users by entering the full email address or phone number you want to reach and start a 1:1 or group chat with anyone with a Microsoft personal account, no tenant switching required. This also means that external Teams Personal accounts users can start conversation with any teams at work users.
Attackers can abuse this feature, which is now enabled by default on all tenants, by sending fraudulent message designed to trick users into revealing sensitivie information to the attacker or deploy malicious software on the victim’s infrastructure like ransomware because media sharing is also enabled by default. This new setting also open a new attack vector for data breaches.
Remediate risk
IT admins have control over the access level for this feature. Below are the control available in the admin center for teams account not managed by an orgranization.
- Outbound chat: enable/disable users in the organization to initiate a chat with external Teams personal accounts users (e.g. users who are not invited guests through Azure AD B2B collaboration). (Enabled by default)
- Inbound chat: enable/disable external users with Teams accounts not managed by an organization to initiate a chat with your users. (Enabled by default)
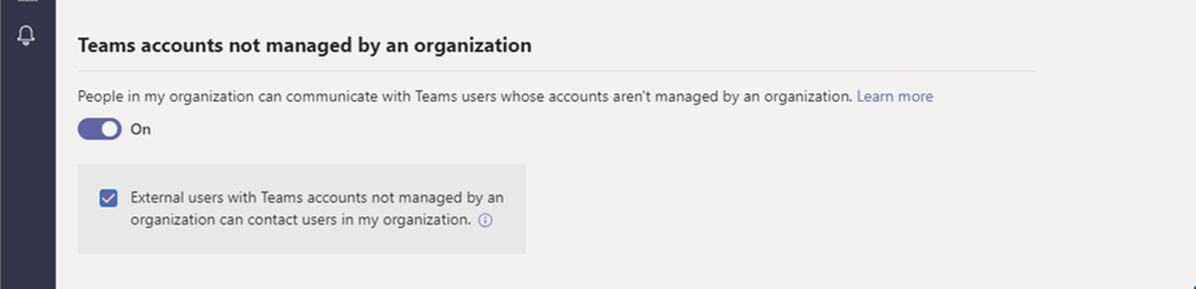
We advise to disable both those settings which will remediate the risk explained above! Later on we will release a new blog with more information about the possible attack vectors in action.
User experience
Below you see an example how the user experience is with this new feature:
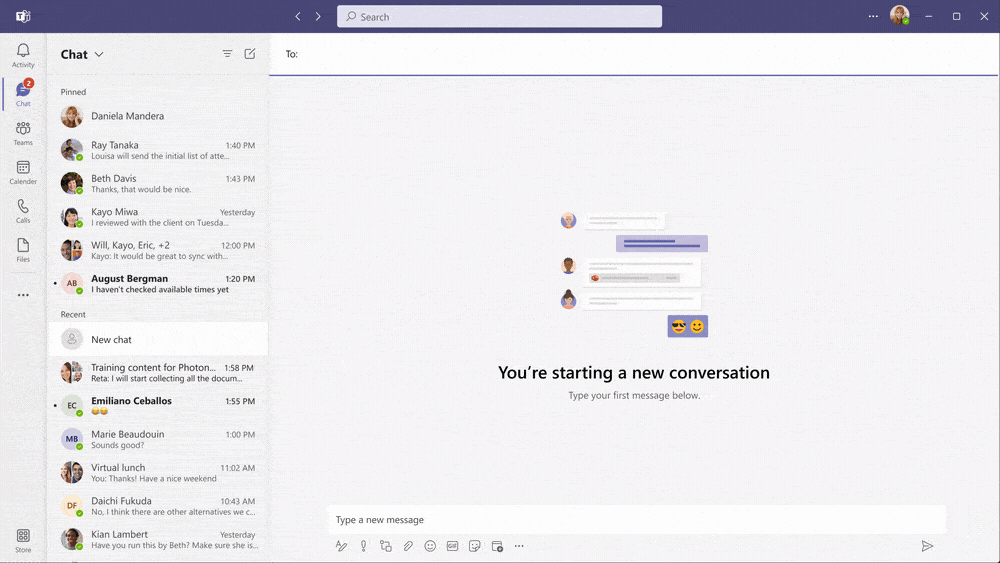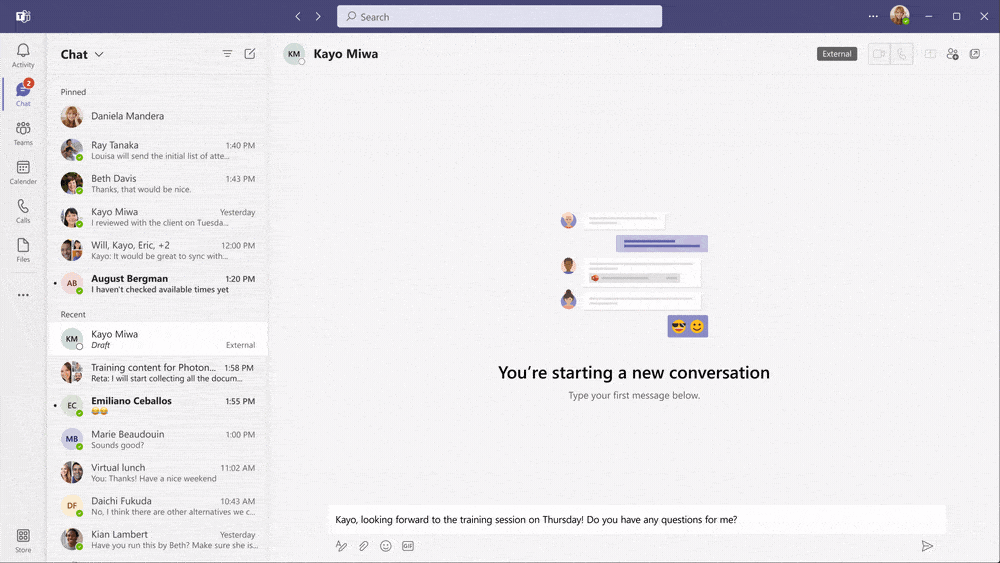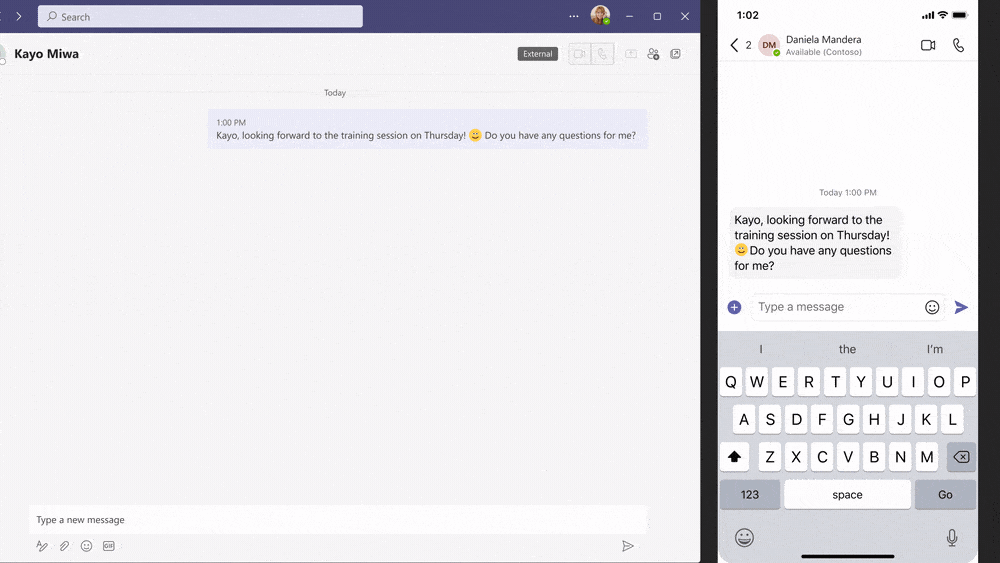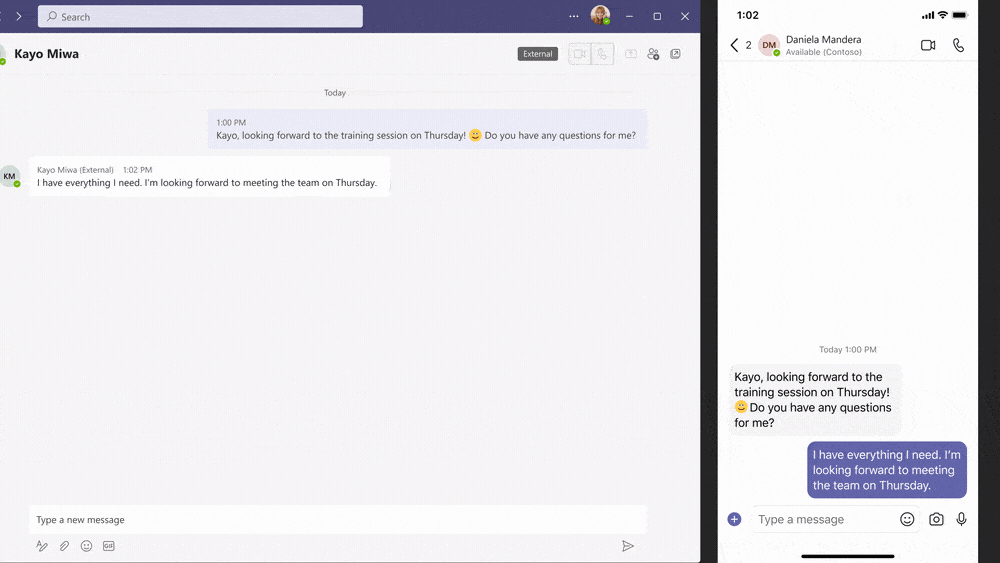
Do you want to know more about how to set up your Microsoft Teams environment in a safer way? Drop us an email on cloudsecurity@secwise.be .

