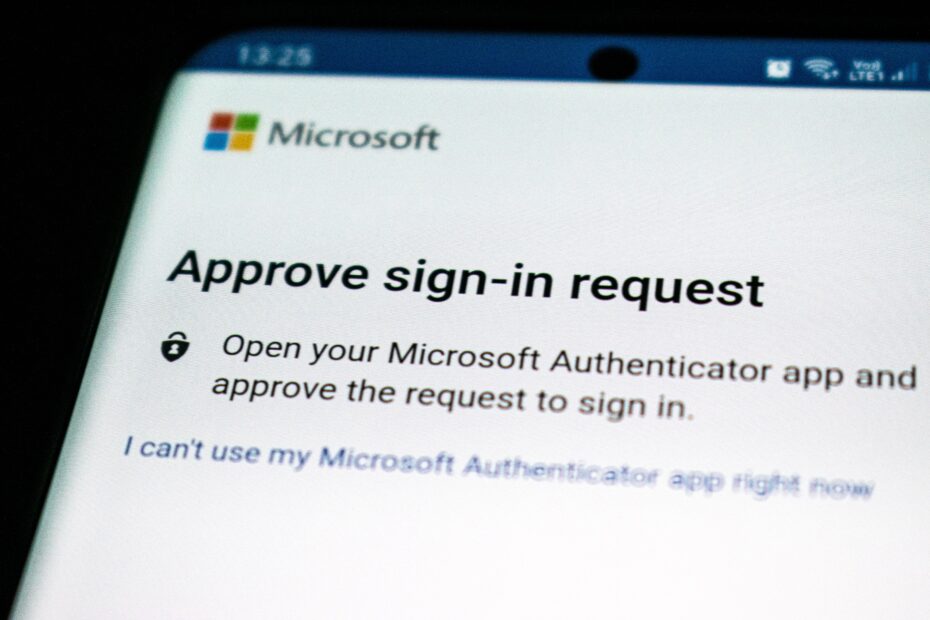
“Are you already using MFA Number Matching?”
MFA Number Matching is a new feature from Microsoft, and a form of Multi-Factor Authentication. It prevents you from accidentally authorising a rogue login attempt by making you enter a two-digit number in your Authenticator app. The feature is suitable for anyone with a Microsoft account using the Microsoft Authenticator app. Cloud security consultant Michiel Schuermans explains below what else to expect from it.
By now, most of us know how MFA works, and believe it’s a secure way to protect ourselves and our accounts. But that is not always the case. Teleworkers probably know it: their company has implemented MFA to secure their accounts. This is a good reflex, but it means that, as a teleworker, you sometimes have to log in via MFA several times a day if you want to access company documents. The risk grows that your employees will almost carelessly give access to company data because they blindly approve an MFA notification.
New Microsoft solution
But what if one of those notifications was not triggered by you, and a hacker tries to get into your account? With Microsoft’s Number Matching, that should be a thing of the past. Instead of just accepting your login, you have to enter a two-digit number. In addition, you will also be shown the location you are logging in from, and which application you want to log in through.
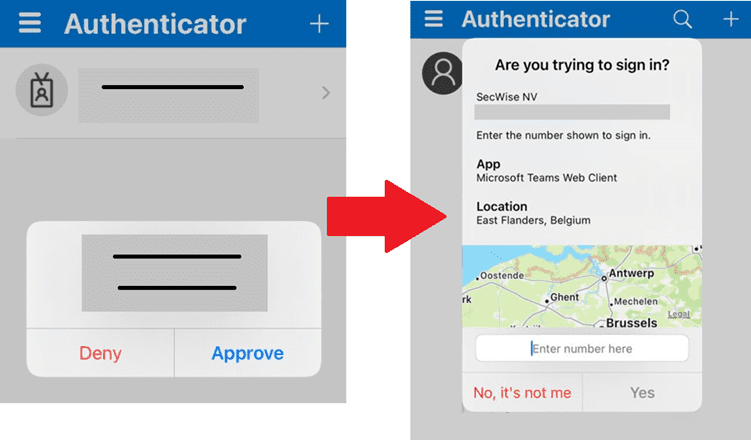
Advantages
This new form of MFA has a lot of advantages. For instance, it is currently one of the most secure ways to log into your Microsoft account. An attacker cannot access the victim’s app, making logging in this way impossible. In turn, the user is notified that someone else is trying to log in to his/her device. Accidental logins are also immediately a thing of the past.
In addition, the app shows a location and the application from which it was logged in. So you can immediately see where the request came from, and whether it matches your location and application. Furthermore, you provide more logging, which your cybersecurity team can then use to track down the attacker.
How do I get started?
Microsoft constantly updates its security policies. Given the many benefits of MFA Number Matching, the feature will therefore be automatically activated for every customer from 27 February. But you can also enable the feature yourself before then, gradually or not.
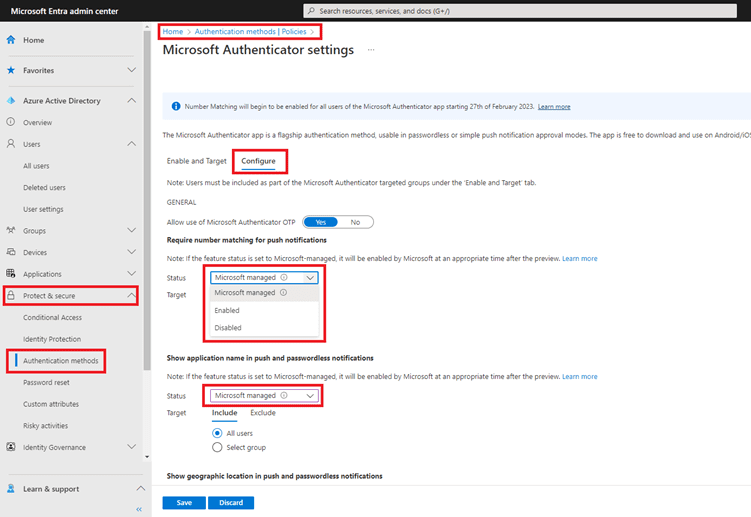
Organisations wishing to enable it manually can contact SecWise for this, or surf to entra.microsoft.com. Go to ‘Protect & Secure’ – ‘Authentication Methods’ and select “Microsoft Authenticator”. Then go to the ‘Configure’ tab. Here you can adjust the settings manually and decide for which user groups you want to deploy the feature.
From SecWise, we advise organisations to notify their employees in advance that a change is coming. That way, everyone is informed of the new function in good time, and you avoid a potentially negative first experience.
You can always find more information about the new function via the following links:
- Number match documentation
- Defend your users from MFA fatigue attacks – Microsoft Community Hub
- Advanced Microsoft Authenticator security features are now generally available! – Microsoft Community Hub
- Additional information
Want to know more about how SecWise can help you secure your cloud or on prem environment? Then be sure to check out our other blogs or leave your details here.