Protecting corporate data with Windows Information Protection
More and more companies are moving to the cloud, to make it easier for end users to access corporate data. As users can now access data from anywhere, both from managed and unmanaged devices, it is a lot tougher for administrators to protect this data. This is especially true for BYOD (Bring Your Own Device) users that are accessing corporate data from their personal devices.
Microsoft has built a solution, Windows Information Protection (WIP), to help organizations easily protect their corporate data accessed from unmanaged devices. One of the biggest advantages of WIP is that it’s built-in to Windows 10, starting from version 1607. So, no need to deploy agent software. WIP allows you to define and enforce policies to apps. The data that is produced by these apps will be protected by policies, without the device needing to be registered in your MDM solution.
How does it work?
Let’s take a simple use case as an example: a user is accessing corporate data from a home computer. An administrator could set a policy to prevent users to copy/paste company information to home computers. Without the need of any device registration, the applications will receive a policy set that is applied simply based upon the username.
Users can use applications to create personal data or corporate data. WIP uses an “allow list” to enforce the policies to the apps, which gives administrators the capability to revoke access to the data if needed. To be able to understand the policies, an application needs to be “enlightened”. This means that the app can distinguish personal from corporate data. In that case the policy will be applied to the corporate data and not to the personal data.
Note that the same exists for Android and iOS devices, called Mobile Application Management (MAM), which is available when the user has an EM+S license.
Conditional Access of Azure AD
So now we know what WIP is and what it can do, we need to make sure that it can be applied each time a user accesses corporate data from any Windows device. This is where Conditional Access of Azure AD comes into play.
You can create a conditional access policy that requires the user to agree with the terms of use and have consent for every device the user logs on with. The devices need to be Azure AD registered before the user can accept the terms of use. When a device is Azure AD registered, it will receive the Windows Information Protection policies.
For the end user, it will look like this the first time he or she tries to access information:
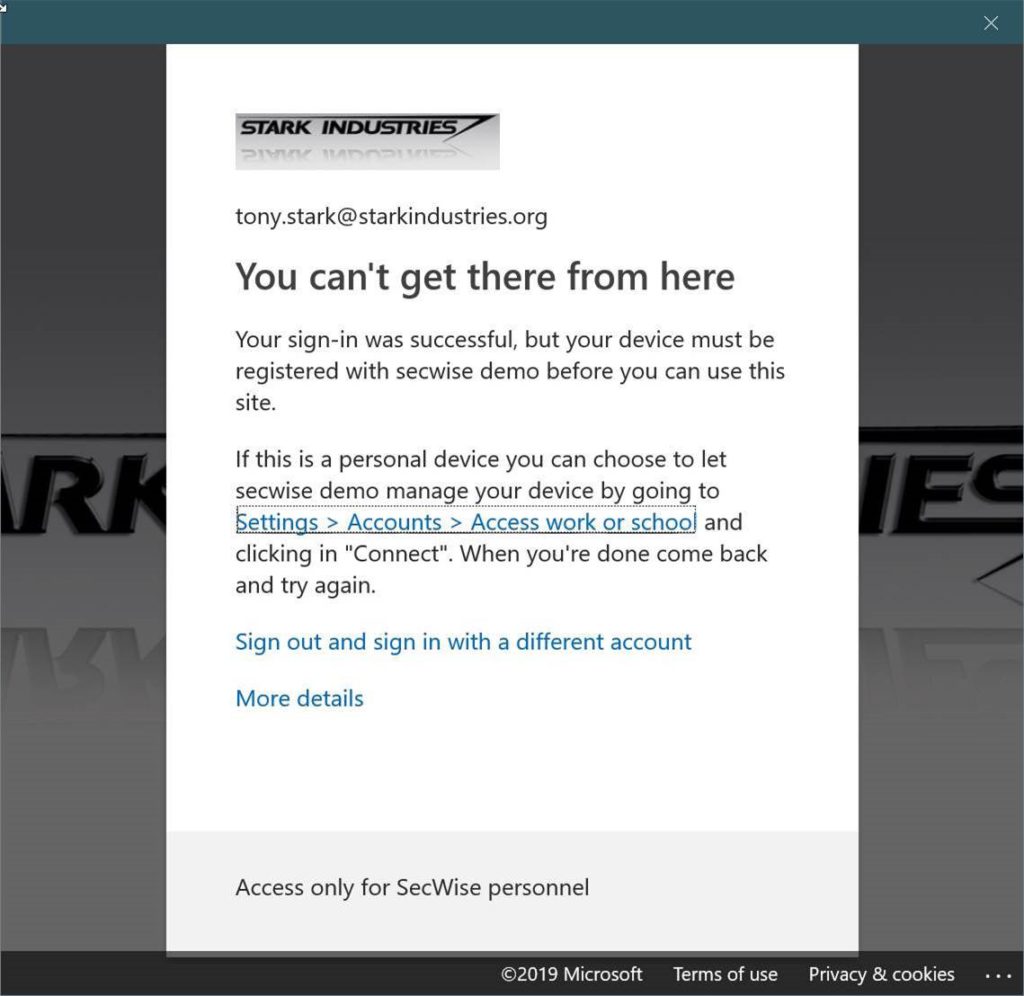
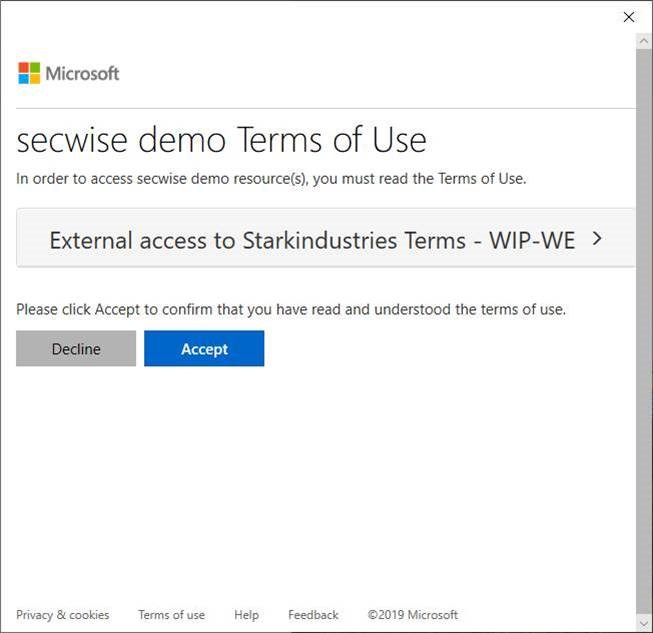
By clicking on the link, the user is sent to the “Access work or school” screen in the settings to register the device. Once the device is registered and the user opens the application, the terms of use need to be accepted:
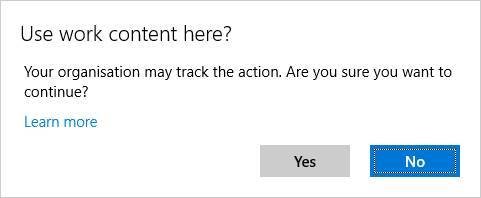
Depending on the policies that have been applied, the user can be blocked from performing copy/paste actions from a work document to a non-work document. In this example the user can copy/paste data, but receives a warning to create awareness that corporate data is being used and that the actions are monitored.
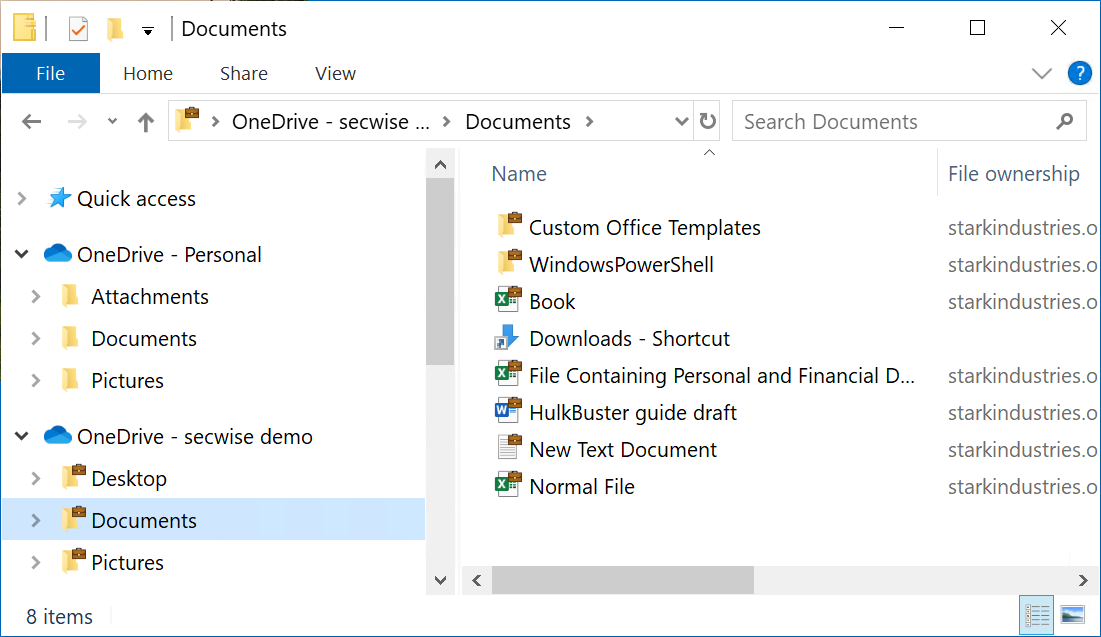
In the screenshot below, you can see that the corporate data has been encrypted as part of the applied WIP policies, which is shown by the “suitcase” icon on top of the folders and files:
WIP’s limitations
Note that WIP has some limitations. The most common ones are:
- WIP is designed for use by a single user per device. As a result, WIP won’t work if the device is registered in one Azure AD tenant while the user is trying to access data from another tenant.
- Only “enlightened” apps can be managed without device enrollment. Currently these apps are:
- Microsoft 3D Viewer
- Microsoft Edge
- Internet Explorer 11
- Microsoft People
- Mobile Office apps, including Word, Excel, PowerPoint, OneNote, and Outlook Mail and Calendar
- Office 365 ProPlus apps, including Word, Excel, PowerPoint, OneNote, and Outlook
- OneDrive app
- OneDrive sync client (OneDrive.exe, the next generation sync client)
- Microsoft Photos
- Groove Music
- Notepad
- Microsoft Paint
- Microsoft Movies & TV
- Microsoft Messaging
- Microsoft Remote Desktop
There is an API available which allows developers to build their own enlightened apps.
Implementing WIP policies
By combining conditional access with the ‘terms of use’ condition, we can enforce a device registration which makes it possible to implement WIP policies. Remember that this works only in BYOD scenarios for users accessing the data from a Windows 10 device.
If the user has left the company, the administrator can remove the device from Azure AD. This will result in the encryption keys being deleted from the client, making the data unreadable on the device.

