This year: Microsoft deprecation of Basic Authentication in Exchange Online
Microsoft has long announced that it is going to block legacy authentication, due to corona and other reasons, this announcement has been delayed. But now there is no escaping anymore and Microsoft will effectively begin on October 1, 2022 to turn off basic authentication for exchange online in all Microsoft 365 tenants regardless of usage, except for SMTP authentication.
Why?
Basic authentication is an outdated authentication protocol. Its threats have only increased since Microsoft originally announced they would disable it. Currently, there are better and more effective modern user authentication alternatives such as OAuth 2.0 token-based authorization. Also For MFA to be effective, you also need to block legacy authentication. This is because legacy authentication protocols like POP, SMTP, IMAP, and MAPI can’t enforce MFA, making them preferred entry points for adversaries attacking your organization… With these threats and risks in mind, Microsoft is taking steps to improve data security in Exchange Online.
Impact
Microsoft also extended the overall impacted scope, the follow protocols are included: Exchange Web Services (EWS), Exchange ActiveSync (EAS), POP, IMAP, Remote PowerShell, MAPI, RPC, SMTP AUTH and OAB.
For Exchange Web Services (EWS), Remote PowerShell (RPS), POP and IMAP, and Exchange ActiveSync (EAS):
- If you have written your own code using these protocols, update your code to use OAuth 2.0 instead of Basic Authentication, or migrate to a newer protocol (Graph API).
- If you or your users are using a 3rd party application which uses these protocols, reach out to the 3rd party app developer who supplied this application to update it to support OAuth 2.0 authentication or assist your users to switch to an application that’s built using OAuth 2.0.
For SMTP AUTH:
Microsoft is going to continue to disable SMTP AUTH for tenants who don’t use it, but we will not be changing the configuration of any tenant who does. But we advise to move away from using Basic and SMTP AUTH though if you can, as it does leave you exposed.
For Exchange Online PowerShell
Since the release of the Exchange Online V2 PowerShell module it’s been easy to manage your Exchange Online settings and protection settings from the command line using Modern authentication. The EXO V2 module uses Modern authentication and works with multifactor authentication (MFA) for connecting to all Exchange-related PowerShell environments in Microsoft 365.
Outlook, MAPI, RPC, and Offline Address Book (OAB)
All versions of Outlook for Windows since 2016 have Modern authentication enabled by default, so it’s likely that you’re already using Modern authentication. Outlook Anywhere (formerly known as RPC over HTTP) has been deprecated in Exchange Online in favor of MAPI over HTTP. Outlook for Windows uses MAPI over HTTP, EWS, and OAB to access mail, set free/busy and out of office, and download the Offline Address Book. All of these protocols support Modern authentication.
What if you want to block Basic authentication?
Here’s a table summarizing the options for proactively disabling basic authentication
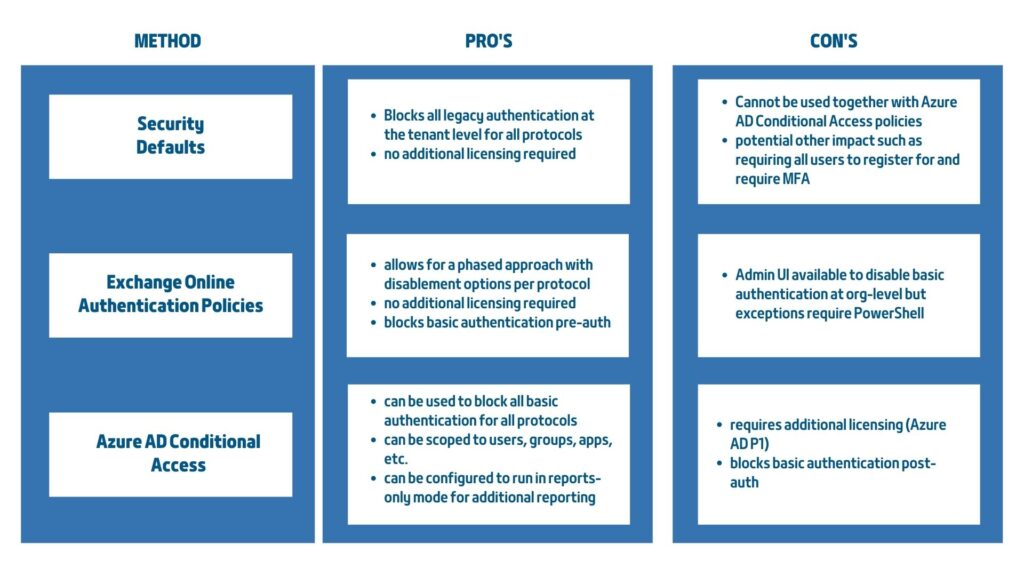
Microsoft will start sending out messages in Microsoft 365 admin Message Center starting from now, informing you that Microsoft are going to disable Basic Authentication for a protocol in your tenant due to non-usage. Or you get one saying we know you are using Basic Auth, but Microsoft intend to proactively disable it for a short period of time, and if you don’t want Microsoft to take that action for protocols in your tenant, you can use a new feature in the Microsoft 365 admin center to request that Microsoft not disable specific protocol(s).
Microsoft added this feature to the self-service tool to help you minimize disruptions as you transition away from using Basic Authentication. But we from SecWise advise you to use this feature only if you really need Basic Auth! Not just because you think you might, or just in case. Customers are compromised through Basic Authentication every day, and the best way to prevent that happening is to disable it and move to Modern Authentication.
You can now go directly to the Basic Auth self-help diagnostic by simply clicking on this link below.
Do you need help with all of your Microsoft questions? Reach out to us!

